
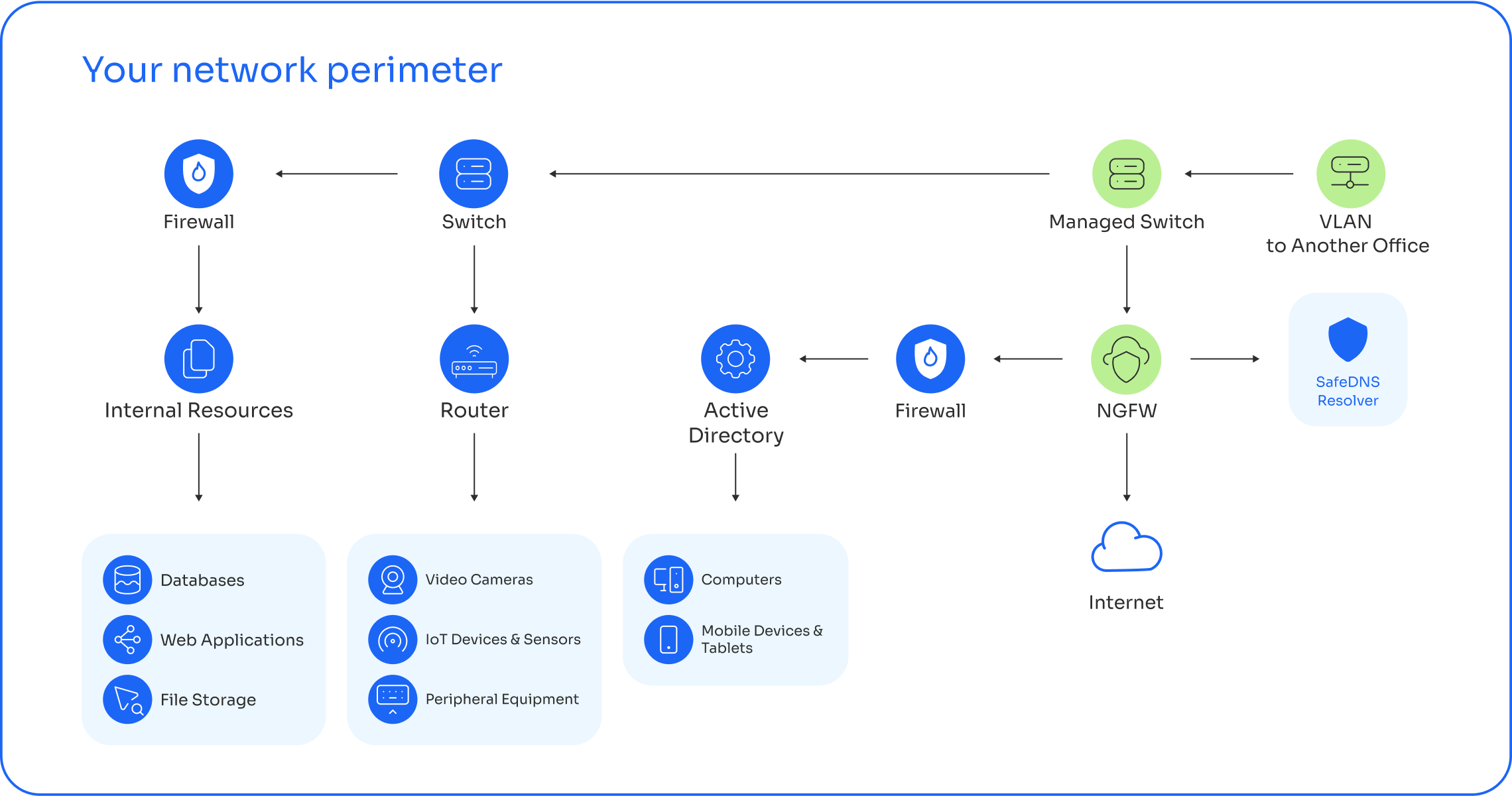
Secure your network beyond the reach of EDR, NGFW, and IDS/IPS
SafeDNS neutralizes hidden threats like phishing, DNS tunneling, malicious scripts
on Cisco/Juniper/MikroTik, IoT attacks, and evasions of NGFW/IDS/IPS. Protect your data and infrastructure starting today

What Happens
When DNS Threats Go Unnoticed
Stealth Data Exfiltration
Malware leveraging DNS tunneling can secretly transmit sensitive data, including credentials, internal documentation, and client databases. By the time monitoring systems (SOC) and security tools (NGFW, IDS, IPS) detect activity, the data is already in the hands of attackers
Full Control Over Infrastructure
By exploiting vulnerabilities in network equipment (Cisco, Juniper, MikroTik), attackers gain administrative access to routers, alter access control lists (ACLs), and reroute traffic through their own servers. This activity often remains undetected by IDS/IPS systems
Hidden threats in IoT Segments
Network devices lacking endpoint protection agents (IP cameras, printers, SCADA controllers) become potential entry points for malware, including trojans and hidden cryptomining modules. NGFW, IDS, and IPS systems typically don’t inspect DNS traffic from such devices, automatically treating it as legitimate
Reputation Damage & Regulatory Fines
A single data breach can expose personal customer data-triggering lawsuits, GDPR fines of up to 4% of annual revenue, and irreparable brand damage through negative media coverage

Total DNS Protection Inside the Perimeter
One platform to block phishing, tunneling, and invisible threats that other tools miss.
We go beyond traditional tools to detect stealthy attacks, compromised devices,
and anomalous behaviors that slip past NGFW, IDS, and EDR.
Phishing & Spoofed Domains
Detects homoglyph domains like aраypal.com vs paypal.com Instantly blocks malicious URLs to stop credential theft and fraud before the page loads.
Tunneling, DGA & C2 Communication
Analyzes DNS patterns to detect encrypted payloads in subdomains.
Instant blocking of DNS tunnels and alerts SOCs of domain generation activity.
IoT and Network Equipment Control
Automatically inventories all DNS-active devices: PCs, servers, routers, printers, cameras.
Flags suspicious behaviors like high NXDOMAIN rates, large TXT queries, or abnormal request spikes.
DoS & DNS Amplification Protection
Intelligent filtering of ANY queries and QPS throttling at the DNS level.
Auto-scaling and failover architecture ensure service continuity even under attack.
Before & After: How SafeDNS Reinforces Your Perimeter
Complete DNS-layer visibility where EDR,
NGFW, and IDS fall short
| Protection Aspect | EDR / Domain Controller | NGFW | SafeDNS |
|---|---|---|---|
| Device Coverage | Only agent-based OS | HTTP/S inspection only, DNS tunneling is invisible | Covers any device making DNS requests-PCs, loT, routers |
| DNS Tunneling / C2 Detection | Depends on endpoint agent, often delayed | Sees volume anomalies, misses DGA patterns | Real-time DNS pattern analysis and resolution-stage blocking |
| Network Hardware Protection | Doesn't monitor router exploits or auto-scripts | Can't detect malicious router scripts; sees spoofed DNS | Detects DNS config anomalies and collects loCs |
| Early Threat Detection | Triggered only by endpoint activity | Delayed response after mass Layer 7 traffic | Warns of DGA/beaconing before business impact |
| loT / BYOD Inventory | Limited to AD/MDM devices | Doesn't identify DNS-only loT traffic | Auto-inventory of all DNS clients — no agents needed |
| DNS DoS / Amplification Defense | Not supported / requires hardware | Partially limits traffic but doesn't scale to DGA storms | DNS Amplification filter, geo-IP throttling, and multi-zone mitigation |
What Sets SafeDNS Apart
Instant Deployment, No Hardware
Deploy in under an hour by changing DNS settings or using DNAT at the firewall. Full network coverage—no agents required
Real-Time Threat Blocking
Phishing domains, C&C servers, DGA-based traffic—all blocked instantly at resolution stage

Full Asset & Device Visibility
Get a complete, live inventory of all DNS-active devices—PCs, IoT, routers,
switches—with user, location, and domain access data
Early Attack Detection
Catch DNS tunneling, brute-force attempts, and internal compromise indicators in the first minutes of activity
SIEM & SOC-Ready
Seamless integration with your SOC
and CMDB: export IoCs, alerts,
and high-level event logs for audit
and response
Resilient, Distributed Architecture
Built for uptime: Active-Active
and Active-Passive clusters, geo-distributed zones, and multi-region failover eliminate single points
of failure


SafeDNS in numbers
73 000 000+
cyber threats blocked daily
5 Billion
daily DNS requests
20 ms
latency worldwide












